First Steps With Browser Meeting
With small steps forward you can get connected to one of the Zoom and Cisco Webex alternatives such as Browser Meeting. After the initial setup and connection set up, you are good to go browsing like never before!
Millions of business users and individuals around the globe are already using VPN. Join them with small easy steps and get your connection even more secure and private.
Follow these simple steps to get on going securely in the cyberworld:
1. Purchase suitable product package from your preferred vendor. Pay attention to any compatibility issues with the devices you plan to use the VPN with.
2. Download the VPN client application and install it to your local operating system. Some products may be launched without installation, just by visiting a designated web page. In these cases your browser might require additional permissions to run the client application (eg. Java).
3. From the VPN client application pick up the server to connect to. In some products you may need to select the exit location separately.
4. Once the connection has been established, your network traffic will encrypted up to the VPN provider. From there all the traffic will travel to their final destination as they normally would.
What’s there under the hood?
VPN connections are becoming increasingly popular as they provide decent level of privacy and encryption for normal network connections.This is done on the networking level to ensure that applications work as usually. Most applications will not notice that you are running VPN. Also all the websites you visit see you coming from the VPN service provider, but on the network level, they see no more.
This all is done by the unique characteristic of a VPN provider. The application you installed created a small tunnel from your computer to the VPN provider. That tunnel is encrypted and acts like a one-way mirror in your car. You can see the Intenet, but they wont be able to see you. If you wont tell them more about you, share your cookies or other identifying information on the application you use, then there remains only a little for a target website administrator to conclude who you are.
Commuting Cyber Citizens and the World
People travel increasingly across the globe, for business and pleasure. Still most of them want to stay online to get the job done. While connected into an unknown network, there is always the looming danger that the wire has been tapped. In the contemporary world where governments and intelligence agencies rush to claim their authority online, this is more relevant than before.
WIth VPN connection set up, you can safely roam almost anywhere in the world.
A lot of new stuff and capabilities
In addition to improved privacy, VPN connection does in fact come up quite a lot of other good things. Routing your traffic across to some specific location may actually result in letting you to enjoy more bandwidth and traffic privileges on the highways of cyberspace.
Furthermore in the old world, many companies did buid their busienss on the assuption that customers come from some specific and rather fixed territory in the cyberspace. With VPN tunneling, some people have even learned how to find out the best flight ticket prices. It is not uncommon to have airlines to sell tickets on lower price for customers depending on which part of the network they are coming from!
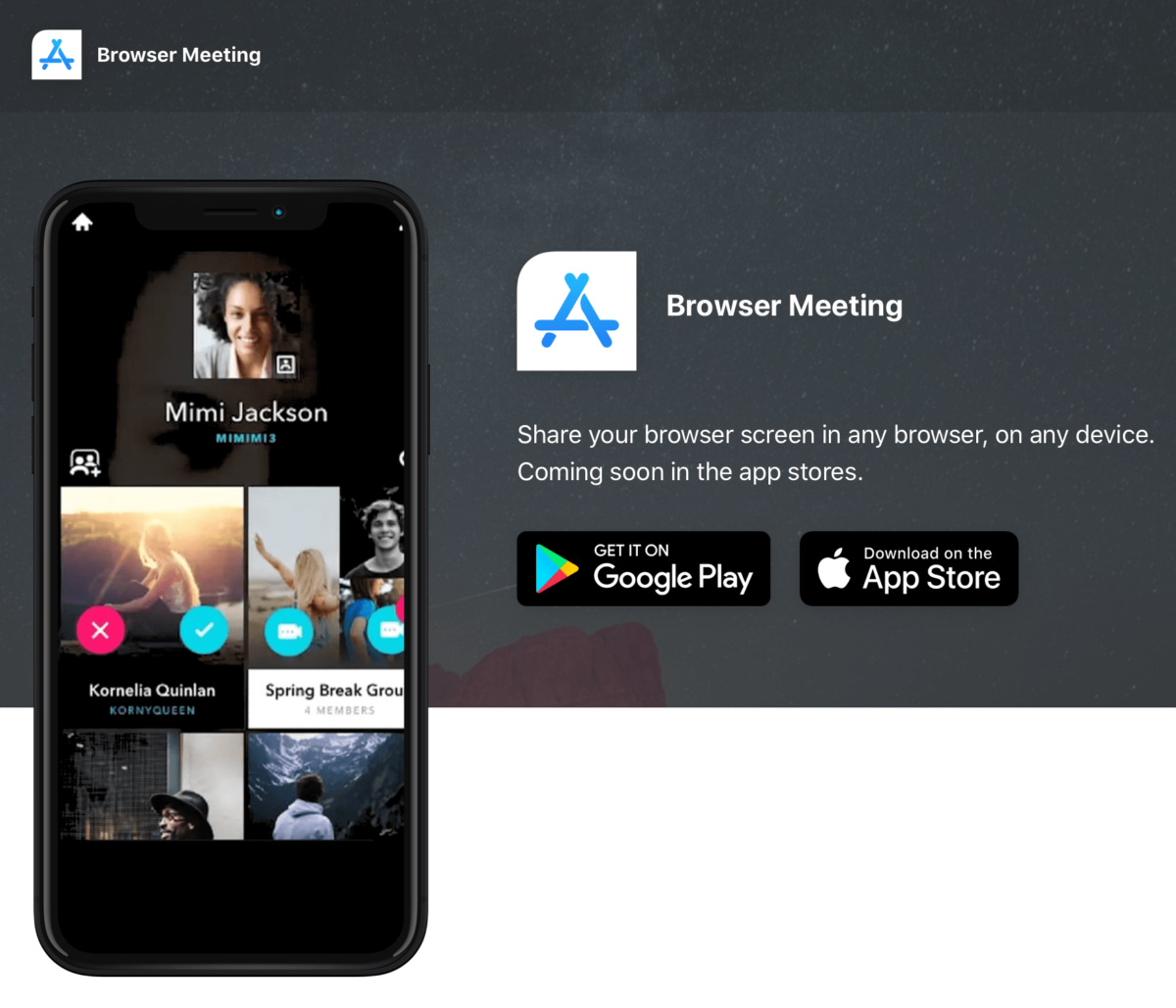
Think about all the movies, languages and interesting people that are there in the world. With Browser Meeting you can easily remote communicate with others just using a web browser like chrome, firefox, brave browser or microsoft edge today.